Gmail users receive strange emails from Google. Should you open them?
 Gmail users are receiving suspicious emails from Google (photo: Unsplash)
Gmail users are receiving suspicious emails from Google (photo: Unsplash)
Phishing has been a dangerous game for many years: as soon as tech companies block one scheme, a new one appears instead. However, a new phishing email has recently circulated, which somehow successfully passes Google's and Gmail's checks, informs Android Authority.
Details of the phishing in Gmail
Developer Nick Johnson reported on X that he became a victim of a sophisticated phishing attack that appeared to come from Google. According to him, the email was sent from the address no-reply@accounts.google.com and was indeed signed as accounts.google.com. Moreover, Gmail showed no warnings.
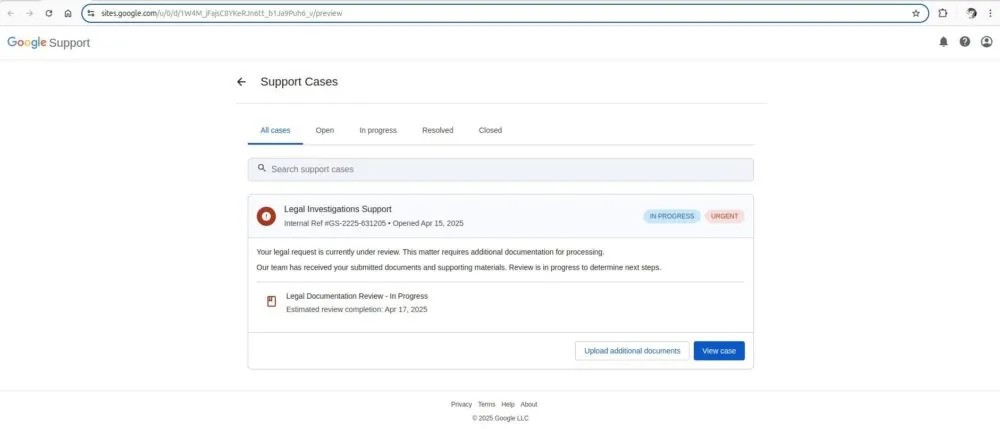
The email contained a link to a page on sites.google.com, which turned out to be a fake support page. It is worth noting that Google Sites is an official Google service that allows users to create websites. It is likely that the attackers chose this platform to deceive users by creating the illusion that they were on an official Google page.
https://x.com/nicksdjohnson/status/1912439027224944676?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1912439027224944676%7Ctwgr%5Ef9d01f2b7b2bd6e258fcd25350d8d42592b7933a%7Ctwcon%5Es1_c10&ref_url=https%3A%2F%2Fwww.rbc.ua%2Frus%2Fstyler%2Fgmail-pochali-prihoditi-divni-listi-vid-google-1744883269.html
When clicking the "View case" or "Upload additional documents" buttons, the user would land on a fake login page, also hosted on sites.google.com.
According to Johnson, this phishing attack was made possible by two vulnerabilities that Google initially refused to fix. First, he suggested that the company disable scripts and arbitrary embedding on Google Sites pages. Secondly, he was concerned that the email was signed as accounts.google.com.
However, if you look carefully at the "mailed-by" field, it shows that it came from the domain privateemail.com.
It turned out that the attackers registered their domain and created a Google account associated with that domain. They then created a Google OAuth app and used the text of the phishing email as the app's name. After that, they gave their Google account access to the created app, which resulted in a security email being sent on behalf of Google. This message was then forwarded to the victims.
Johnson reported the vulnerability, but Google initially closed the report, claiming that such behavior was normal. However, later the company changed its decision and agreed to fix the authentication issue.
In any case, this is an extremely convincing phishing attack, and users should be particularly cautious.
It is worth noting that a similar scheme had been previously reported: users were sent fake security recovery emails supposedly from Google, and there were also calls from fake Google support numbers.
Request to support service (photo: X/NicksDJohnson)

